Ensure All-Round Cloud Data Warehouse Security With these 3 Measures

Audio : Listen to This Blog.
The volume, scope, and severity of cyberattacks seem to be swelling with the sudden rise in remote business interactions. Reportedly, Australian multi-national banking and services firm ANZ has had data breaches in 47% of its businesses. This raises the question that with organizations collecting data blocks from any and every source they can get their hands on – How secure are our storage resources?
Cloud Data warehouse holds data from multiple sources, including internal audits, customer data, marketing feedback, and more. Protecting such critical business influencing data cannot be left to the usual cloud storage security measures we employ. We need network security and access control methods that are specific to the cloud data warehouse architecture. How do we go about it, and what are these security methods exclusive to the needs of a cloud data warehouse? This would be the prime discussion in this blog.
Security Overview for Cloud Data Warehouse
The cloud data warehouse vendors like Amazon Redshift, Azure SQL warehouse, etc., have multiple security procedures dedicated to protecting the cloud warehouse data. The API calls are monitored and controlled for their access. Clients are encouraged to support appropriate security layers like TLS 1.0 or later. The data is encrypted with forwarding secrecy ciphers like Diffie-Hellman (DHE). The request authorization is controlled using access IDs, security groups, etc. Some vendors also use temporary security credentials for certain requests. Resource based access also allows the cloud data warehouses to restrict resource access for certain source IPs.
Broadly classifying the dedicated security measures for cloud data warehouse would leave us with:
- Network Security
- Cluster Security
- Connection Security
We will now discuss these three security aspects one by one.
Network Security
For cloud data warehouses, network security is worked through network isolation. Most of the venders prefer logically isolated and virtually private cloud networks where the clusters can be deployed using the following steps:
Step 1 – A logically isolated network layer is created using specifics like – Subnet, routing table, network gateway, and network endpoints.
Step 2 – The allocation and aggregation of the network are done using Classless Inter-Domain Routing (CIDR).
Step 3 – Interfaces like consoles, CLIs and SDKs, are created to access the networks.
Step 4 – Two or more subnets are created for dedicated accounts.
Step 5 – The cluster is deployed in the network.
The cluster can be locked down for inbound network traffic. You can decide which IP addresses are permitted to access the cluster in your network. Therefore, the network is all secure to entertain the client request, and what remains is to secure the clusters themselves.
Cluster Security
Generally, the cloud data warehouses have the cluster locked for access by default. They are later granted access as per the resources requirement and process handling they are deployed for. An effective way to do this is by categorizing the clusters into security groups. These security groups define the access control depending on the network subnet provisioned for the cluster. Vendors like Amazon Redshift have default as well as customized classes called the security groups. With customized classes, one can define access policies by themselves.
The policies that categorize these security groups generally are meant to identify a range of IPs that are permitted to access the corresponding clusters. The classes can be created with or without a cluster provisioned to them. The inbound access policies can be defined for the group and the cluster can be launched later. There are mainly three kinds of interfaces that can be employed to create security groups.
- GUI Consoles – GUI consoles can help to create security groups on the basis of details like class name, CIDR range, IP authorization details, and user account authentication details. These consoles are offered internally by most of the cloud data warehouse vendors. They can also be used to define the access policies for the group.
- CLI Commands – Most of the cloud vendors also offer CLI commands for creating the security groups, adding or revoking the access policies, and managing the clusters
- SDKs – Open source codes for Java or AWS SDKs are available for managing the security groups. The default code doesn’t have any ingress rules, and they can be added to the code as per the CIDR range required.
With clusters and subnets secured using security groups, additional security can be ensured by securing the connections that access these networks and clusters.
Connection Security
The connection security majorly deals with securing the endpoints on the connections. Any API requesting a connection with the cluster can be provided access using a secure endpoint like Virtual Private Cloud (VPC) instead of a public network. With the endpoint secure, the ODBC and JDBC connections can establish the communication between the client and the warehouse more securely. The endpoint security can be ensured using resources like – VPNs, Internet gateways, network address translation, or like Amazon Redshift, directly accessing the AWS Network.
The private connection can be created with a secure DNS that can be customized or offered by the vendor.
Here are some of the code snippets for a different kind of VPCs offered by AWS:
Denying all access
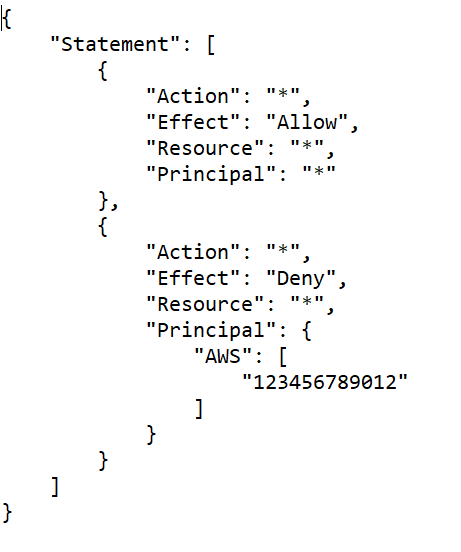
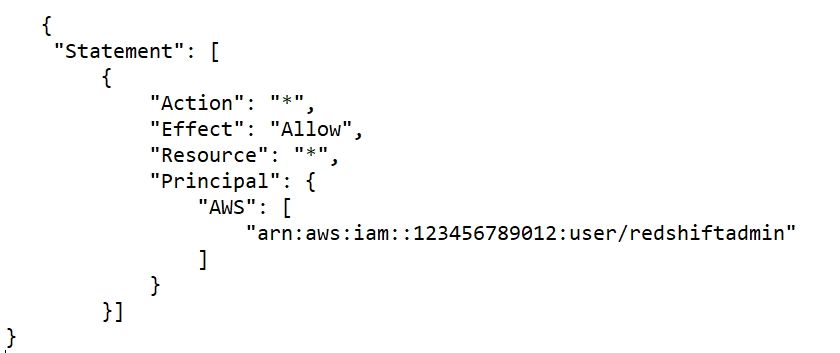
Specific User Access
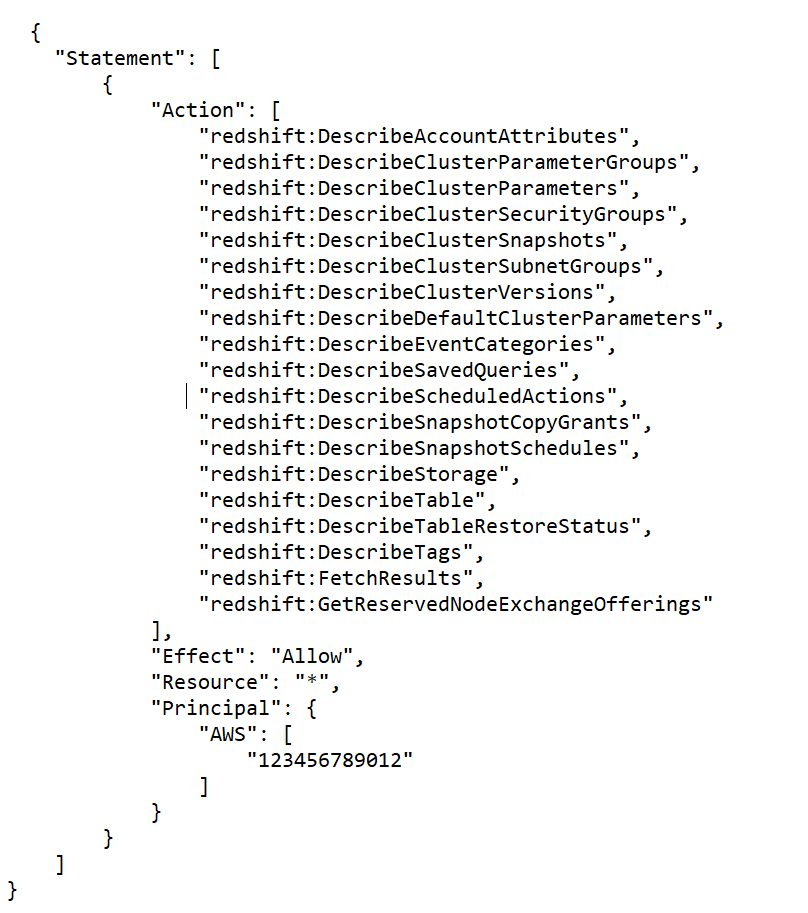
Read-Only Access
End-point security also protects the network from use prone access issues. With the network, clusters, and API requests secured, the additional layers for cloud storage security can ensure that the organizational data is all safe for business.
Security Monitoring
Apart from the above discussed measures, it is also necessary that the warehouse is constantly monitored for security misbehavior. Consistent monitoring of the network, workload and clusters from a security point of view can be configured with regular reports on surface level dashboards.
Final Thoughts
Cloud Data warehouses are all set to churn out influential business insights through the data being fed to them from multiple sources. While this makes them a gold mine for pioneering business ventures, they also become a target for security breaches, data losses, and network attacks. Therefore, apart from the security and data protection available for cloud storage infrastructures, these warehouses would need specific security measures that align with their own architecture. With the measures discussed above, you can rest assured of the knowledge and intelligence that the cloud warehouse has to offer.
